
At its core, a transaction monitoring solution is a bit like a digital security guard for your business's finances. It's an automated system that keeps a constant eye on every single payment coming in and going out, flagging anything that looks out of place or breaks a specific rule. Its main job is to protect your business, keep you on the right side of compliance, and build trust with your customers.
Understanding Your Digital Security Guard

Think of it like a neighborhood watch program, but for your company’s money. In a neighborhood watch, residents get to know what’s normal—who lives where, what cars are usually parked on the street, and the general rhythm of the day. If a strange car starts circling the block at 3 AM, people notice because it deviates from that established pattern.
A transaction monitoring solution works in much the same way. Instead of watching streets, it’s watching your flow of payments.
Establishing What’s Normal
First, the system has to learn what "normal" activity actually looks like for your business. This baseline includes things like average purchase amounts, where your customers are usually located, and your peak sales times. It’s the digital equivalent of knowing your neighbors' routines. This first step is absolutely critical for spotting real threats accurately later on.
Once that baseline is set, the system kicks into real-time surveillance. Every transaction gets analyzed against these established patterns and a set of specific rules designed to catch common red flags.
Key Takeaway: Transaction monitoring isn't just about catching fraud after the damage is done. It’s a proactive defense system built to identify suspicious activity the moment it happens, minimizing the potential hit to your revenue and reputation.
To give you a clearer picture, here's a simple breakdown of what these systems are doing behind the scenes.
Core Functions of Transaction Monitoring at a Glance
Ultimately, these functions work together to create a powerful safety net for your business.
Why This Matters for Every Business
It doesn’t matter if you run a small online shop or a large financial service—this kind of protection is vital. The need for these robust systems has fueled some serious growth in the market. Valued at roughly USD 11.8 billion in 2025, the global transaction monitoring market is projected to nearly quadruple to USD 44.3 billion by 2035. According to Future Market Insights, this explosion shows just how essential these tools have become for managing risk and staying compliant.
This proactive monitoring is your first line of defense, helping you stop problems that could easily turn into financial loss or painful chargebacks. To learn more about handling disputes after they’ve already happened, check out our guide on what chargeback management is and see how it fits in with a strong fraud prevention strategy. By combining both, you ensure your business is protected from every angle.
How These Systems Actually Work
So, how does a system actually sniff out a "suspicious" transaction? It’s not magic, but it's a pretty smart, logical process.
Think of it like your credit card company calling to ask if you really just bought a fancy lawnmower three states away. They noticed something that didn't fit your usual pattern, and that’s the core idea behind transaction monitoring solutions.
It all starts with defining what "normal" looks like for your business. This isn't a one-size-fits-all deal; you have to set up a baseline by creating rules based on your typical customer behavior, average sale amounts, and common purchase locations. This basically creates a unique financial fingerprint for your store.
Once those rules are locked in, the system gets to work, collecting data from every single payment in real-time. The real action happens when it compares each new transaction against your established rules and past activity. It’s constantly asking questions: Is this purchase amount way higher than usual? Is the customer's location totally different from their past orders? Are there a bunch of rapid-fire attempts coming from the same IP address?
From Rules to Real-Time Alerts
This simple, three-step process—defining rules, collecting data, and analyzing for anything weird—is the foundation of how these systems operate.
This infographic breaks down that fundamental flow, showing how rules, data collection, and analysis work together to spit out an alert when something’s off.
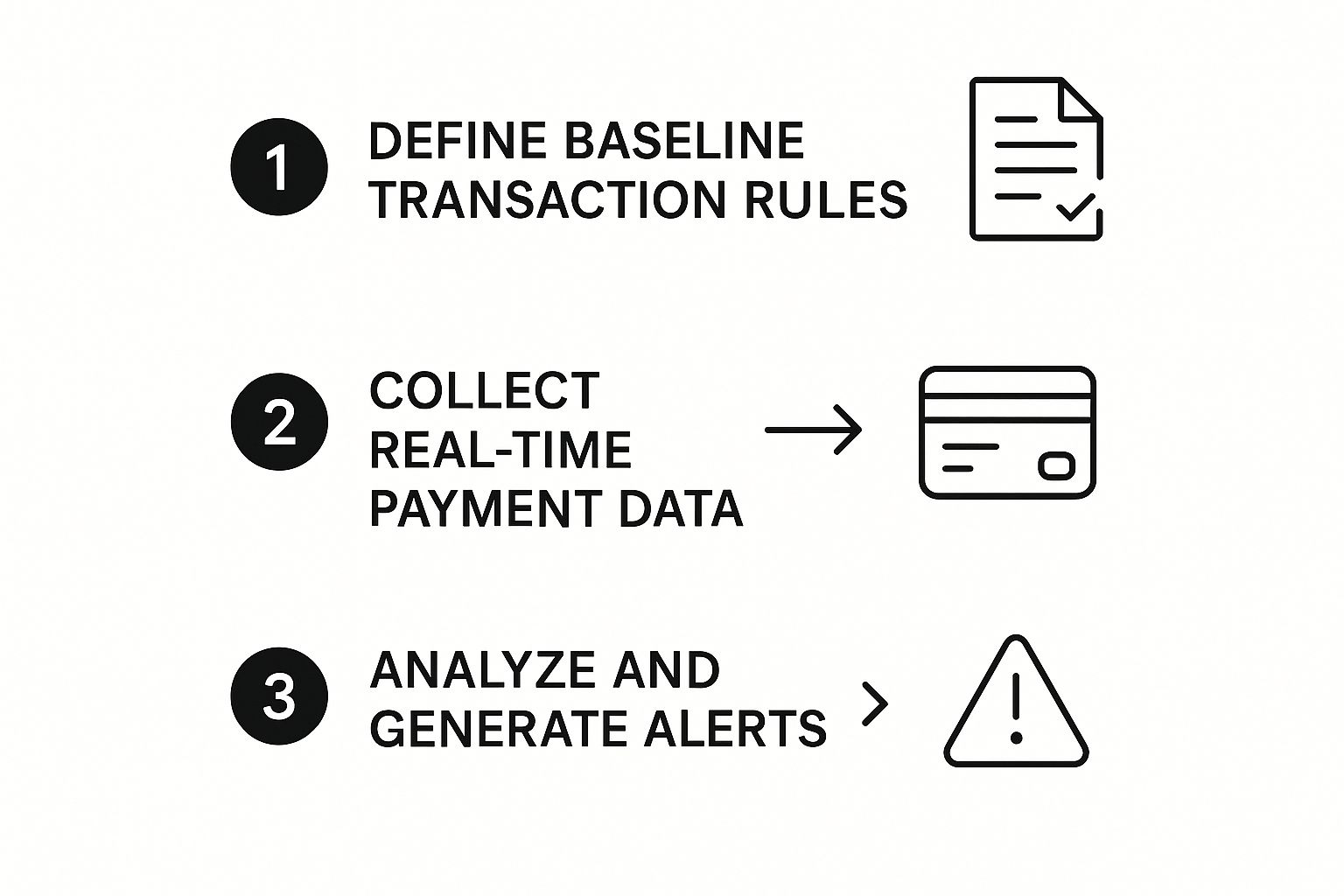
As you can see, the system's power comes from its ability to instantly connect live transaction data with the security rules you've already defined.
The most basic version of this is rule-based monitoring. You set clear instructions, like "flag any transaction over $5,000" or "alert on five transactions from the same card in under 10 minutes." If a transaction breaks one of these rules, an alert gets automatically generated for someone to look at. This method is great for catching known and obvious fraud patterns.
But modern systems go a step further with behavioral analysis. Instead of just following rigid rules, they actually learn the rhythm of your business. By using AI, they can spot subtle changes that wouldn't necessarily trigger a specific rule but are still highly suspicious. This adaptive learning is a game-changer for identifying new and evolving fraud tactics.
Key Insight: The best transaction monitoring solutions blend predictable rule-based alerts with intelligent behavioral analysis. This combination allows them to catch both the common threats you know about and the unexpected ones you don't.
For businesses working in decentralized spaces like crypto, understanding these flows requires a different skillset. Mastering blockchain data analysis is key to applying these monitoring principles to on-chain activities.
Ultimately, this whole process is designed to feed into a smoother workflow. When an alert is triggered, it doesn't just sit there. It kicks off an investigation that often ties directly into your dispute management process. For a deeper dive, check out our complete guide to automated chargeback management to see how these systems work together to protect your bottom line.
Must-Have Features in a Monitoring Solution

When you’re looking at different transaction monitoring solutions, it’s easy to get lost in a sea of technical jargon. But let’s cut through the noise. At the end of the day, you need a tool that actively protects your business without creating a mountain of extra work.
Think of it less like buying software and more like hiring a new member of your security team. You want someone fast, smart, and easy to work with. Not all systems are built the same, and a few key features separate a basic tool from a powerful security partner.
Core Capabilities for Any Business
First things first: the system absolutely must operate in real-time. Fraudsters don’t wait around, and a delay of even a few minutes can be the difference between blocking a bad payment and dealing with a costly chargeback. The power to analyze and flag a transaction the second it happens is non-negotiable.
Equally important are customizable rules. Your business isn’t a carbon copy of another, so a one-size-fits-all approach just won’t cut it. You need the flexibility to create and tweak rules that reflect your specific products, customer behavior, and risk appetite. This ensures you’re catching relevant threats, not just generating a bunch of useless noise.
Another must-have is a user-friendly dashboard. The best data in the world is worthless if you can’t make sense of it. A clear, intuitive dashboard that visualizes alerts, trends, and key metrics allows your team to make faster, smarter decisions—no data science degree required.
It's no surprise the market for these tools is booming. The transaction monitoring software market was valued at USD 18.31 billion and is projected to skyrocket to USD 50.25 billion by 2033. This massive growth is driven by the clear need for smarter security in an increasingly digital economy. You can find more insights about this expanding market from IMARC Group.
Advanced Features That Make a Difference
Beyond the basics, a few advanced features can seriously level up your defenses. Link analysis is a game-changer. It helps your team uncover hidden connections between what look like unrelated accounts or transactions. By spotting shared details like IP addresses or device IDs, it can expose entire fraud rings trying to hit your business.
Key Insight: A top-tier monitoring system should also incorporate machine learning. This allows the tool to adapt on its own, learning your "normal" transaction patterns and spotting new, sophisticated threats that your pre-set rules might miss.
Finally, effective case management is essential for streamlining your team’s workflow. When an alert pops up, the system should give you all the necessary context in one place, making investigations quick and painless. This capability is one of the most important features to look for in different chargeback management tools, as it perfectly bridges the gap between detecting a problem and actually solving it.
Stopping Common Fraud Scenarios

To really get why a strong defense matters, you have to understand the attacks it’s built to stop. Transaction monitoring isn't just a background process; it’s designed to sniff out specific criminal behaviors that can hit your bottom line and tarnish your reputation. Looking at a few real-world examples shows you exactly how these systems turn suspicious data points into alerts you can actually use.
Let's start with a classic: credit card fraud. Picture a fraudster who just bought a list of stolen card numbers. Their first move is often to test the cards with tiny purchases—maybe a $1.00 digital download—just to see if they're active. If that charge goes through, they immediately hit it with a much bigger purchase before the real owner even gets a notification.
This is where a good monitoring system earns its keep. It instantly flags this behavior as a major red flag.
How it's caught: A rule flags the unusual sequence of a tiny transaction followed by a large one from the same card within minutes. The system can automatically block the second transaction and alert your team, stopping the loss before it ever happens.
Unraveling Complex Schemes
Of course, criminals do more than just steal card numbers. More complex methods like account takeover (ATO) are on the rise. In this scenario, a fraudster gets into a legitimate customer’s account, changes the shipping address, and then places a huge order for high-value items. They're banking on the transaction looking normal because it’s coming from a trusted account.
A transaction monitoring solution spots this by looking beyond the purchase itself. It’s all about context.
- Sudden Changes: The system detects that the account’s shipping address was changed just moments before a major purchase. That’s a huge red flag.
- Device Mismatch: It also notes the login came from a completely new device or a different geographic location than the customer’s usual activity.
- Behavioral Shifts: The purchase itself—maybe for three high-end laptops when the customer usually buys t-shirts—is a major departure from their established buying habits.
This combination of alerts paints a clear picture: the account is very likely compromised. If you want to dive deeper into securing your business, our guide on eCommerce fraud prevention lays out additional strategies to protect your store.
To give you a clearer picture, let's break down how monitoring tools respond to different types of fraud.
Fraud Scenarios and Monitoring Responses
These examples show how a monitoring system piece together clues that would be nearly impossible to spot manually, especially in real-time.
Following the Money Trail
One of the most serious financial crimes out there is money laundering. Criminals need a way to make dirty money look clean. A common tactic is "structuring," where they break up a massive sum of cash into tons of small, less-suspicious deposits into an account. Once the money is in, they might try to wire the whole amount overseas.
Individually, each tiny deposit might fly under the radar. But a powerful transaction monitoring solution is built to see the entire forest, not just the trees. It connects these seemingly separate events and identifies the pattern—multiple small deposits followed by a single large international transfer.
This is a textbook money laundering indicator, and the system flags it for immediate human review. For those curious about the tech that makes this possible, resources on Neo4j real-time analytics for fraud detection offer a great look at how these systems connect the dots instantly. By recognizing these common schemes, it becomes clear that transaction monitoring isn't just a defensive tool—it's an essential part of doing business safely and responsibly.
Integrating Monitoring with Your Payment System
Knowing how to spot fraud is one thing, but actually stopping it is what really matters. The true power of a transaction monitoring solution comes to life when you plug it directly into your payment system. This isn't just some technical tweak; it's a strategic move that builds a unified defense around your business.
Think of it this way: your payment processor and your monitoring tool are like two separate security guards. When they don’t talk, one might see a suspicious character lurking, while the other unknowingly holds the door open for them. Integration gets them on the same radio frequency, sharing info instantly to make smarter, faster decisions.
This seamless connection means your payment processing and fraud detection are in constant conversation. When the monitoring system flags a high-risk transaction, it can shout that information back to your payment gateway in real time, creating a powerful, automated shield.
Creating a Seamless Defense
Integrating these systems completely changes your security from reactive to proactive. Instead of just reviewing alerts after a fraudulent transaction has already gone through, you're creating an environment where sketchy payments can be stopped in their tracks—before they're ever completed. This connection is the key to minimizing risk and protecting your bottom line.
And the benefits go way beyond just blocking bad guys. A tightly integrated system also seriously boosts your team's efficiency and improves the overall experience for your legitimate customers.
Here’s what that looks like day-to-day:
- Automated Dispute Responses: When a flagged transaction does turn into a chargeback, the integrated system can automatically pull all the relevant monitoring data to build a much stronger, evidence-backed dispute response.
- Fewer False Positives: By sharing data back and forth, the system gets smarter about what real fraud looks like for your business. That means fewer legitimate customers get their payments wrongly declined.
- Faster Investigations: Your team gets the full story on every transaction. Payment details and fraud risk scores live in one place, giving them a unified view to make quick, informed decisions.
A unified approach means you’re no longer managing payments and fraud in separate silos. You're building an intelligent, connected ecosystem that protects your revenue, saves your team time, and keeps your good customers happy.
Connecting with Payment Platforms
Modern transaction monitoring solutions are built to play nice with major payment processors like Stripe and PayPal. This integration is the backbone for platforms like ChargePay, which uses this shared data to automate chargeback representment.
For instance, you can see how this synergy works in the real world by learning more about how ChargePay integrates with PayPal for chargeback management.
At the end of the day, this isn't about just adding another tool to your stack. It's about making your existing systems work together to create a defense that is far stronger and more efficient than the sum of its parts.
Best Practices for Managing Your System
Setting up a transaction monitoring solution is a huge step forward, but it’s definitely not a “set it and forget it” kind of tool. To get real, lasting value, you need a smart approach to managing it day in and day out.
Think of it like a garden. You can’t just plant the seeds and walk away expecting a great harvest. You need to water, weed, and adapt to the changing seasons to keep it healthy and productive. The same logic applies here.
The single most critical practice is to regularly review and update your monitoring rules. Fraudsters are always changing their tactics, and what worked six months ago might be completely useless today. Your business evolves, too—maybe you're launching new products or expanding into new regions. These changes require you to tweak your rules to reflect new, "normal" transaction patterns.
Keeping Your Team Sharp and Ready
Technology is only half the equation. The human element is just as critical, if not more so. Your team needs to know exactly what to do when an alert pops up. This all starts with proper training on how to investigate alerts efficiently, separating the real threats from the false alarms.
A well-defined process is absolutely essential. Every analyst should follow the same clear, documented steps for handling a flagged transaction. This consistency not only speeds up investigations but also makes sure your responses are fair, accurate, and defensible if regulators ever come knocking.
Key Takeaway: A monitoring system is a living part of your business's defense. It requires continuous attention—from rule updates to team training—to stay effective against threats that are always shifting.
Staying Aware of Global Trends
Part of managing your system is understanding where the next wave of threats might come from. For instance, the demand for effective AML compliance is surging worldwide, and you need to be ready for what that means for your business.
Regionally, Asia Pacific is quickly becoming the fastest-growing market for these solutions, projected to capture about 46% of the revenue share by 2035. This growth is largely a response to increased financial crime in the area, which highlights just how global these security challenges are. You can explore more insights about this global market growth on Research Nester.
By keeping an eye on these kinds of trends, you can proactively adjust your monitoring strategy to get ahead of future risks.
Frequently Asked Questions
Still have a few questions floating around about transaction monitoring? You're not the only one. Let's tackle some of the most common ones we hear.
Is Transaction Monitoring Just for Big Banks?
Not at all. While you definitely see these systems in big financial institutions, any business that takes payments online is a target for fraud.
Whether you're running an e-commerce store, a subscription service, or a fintech startup, these tools are essential for protecting your revenue. Modern solutions are built to grow with you, making them a great fit for businesses of any size.
Will This Slow Down My Checkout Process?
Nope. A well-designed system does its magic in the background, in real time, without getting in your customer's way. The analysis happens in milliseconds, so your legitimate customers won't even know it's there.
The whole point is to be invisible to good customers while putting up a massive roadblock for fraudsters.
A common myth is that more security has to mean more friction. With today's transaction monitoring solutions, the goal is to be invisible to legitimate users while being impossible for threats to ignore.
What’s the Difference Between Rule-Based and AI-Based Monitoring?
Think of it like this: rule-based monitoring is like a bouncer with a checklist. It flags anything that breaks a specific, pre-set rule, like "block any purchase over $1,000 from a new country." It's straightforward and effective for obvious threats.
AI-based monitoring, on the other hand, is more like an experienced detective. It learns the normal rhythm of your business and can spot suspicious behavior that might not break a specific rule but just feels off. It's looking for the subtle patterns that a simple checklist would miss.
For the best protection, most modern systems blend both approaches, giving you the best of both worlds.
Ready to shut down fraud and put chargeback recovery on autopilot? With ChargePay, you can protect your revenue with an AI-powered solution that works seamlessly with your payment system. Discover how ChargePay can secure your business.







.svg)







.svg)
.svg)
.svg)