
Payment tokenization is how sensitive payment card details get swapped out for a unique, non-sensitive equivalent called a token. This token is just a randomly generated string of characters that stands in for the actual card number. It has no real value on its own, making it completely useless to fraudsters if they ever get their hands on it.
Understanding What Is Tokenization in Payments
Ever wonder how your credit card details stay safe when you buy something online? Or how services like Amazon can offer one-click checkouts without constantly asking for your card number? The secret behind it all is payment tokenization. It's a security method that acts like a digital bodyguard for your most sensitive financial information.
Think of it like using a casino chip instead of cash. Inside the casino, that chip has a clear value and you can use it to play games or buy a drink. But the moment you step outside, it's just a worthless piece of plastic. A payment token works the exact same way—it only has meaning within a specific payment system and is gibberish to anyone outside of it.
The Key Players in the Process
To really get how this all works, it helps to know who the main players are. Every time you make a purchase, a few key entities are working together behind the scenes, each with a critical role in keeping your data secure.
This collaboration is designed to make sure your real card number is exposed as little as possible, drastically cutting down the risk of it being stolen and misused. For a deeper dive into how payments are handled from start to finish, you can learn more about what a payment processor is and its role in the whole system.
Here’s a quick rundown of who does what in the tokenization dance:
Key Players in the Tokenization Process
Essentially, each player passes the baton securely, ensuring your actual financial information stays locked away and protected from prying eyes.
How Payment Tokenization Works Step by Step
Okay, so we know who the key players are. Now, let’s follow your payment details from the second you hit that "buy" button. It might sound like a lot is going on, but this all happens in the blink of an eye, broken down into a few key steps designed to keep your information locked down.
The whole point of this system is to make sure the merchant never has to handle or store your actual credit card number. That's a massive win for security.
The magic starts the moment you type in your card details and submit your order. This kicks off a secure, behind-the-scenes dance that protects your data at every turn.
Step 1: Data Capture and Encryption
The first move happens right there on the merchant's checkout page or payment terminal. When you enter your 16-digit card number, expiration date, and CVV, that information is encrypted on the spot. It's instantly turned into a scrambled code before it even leaves your browser.
This initial encryption is your first line of defense. It means that even if a cybercriminal was somehow snooping on the transaction, all they’d see is unreadable gibberish, not your actual card details. This encrypted bundle of data is then sent securely to the payment gateway.
This simple infographic shows how your card data is swapped for a secure token that the merchant can safely use.
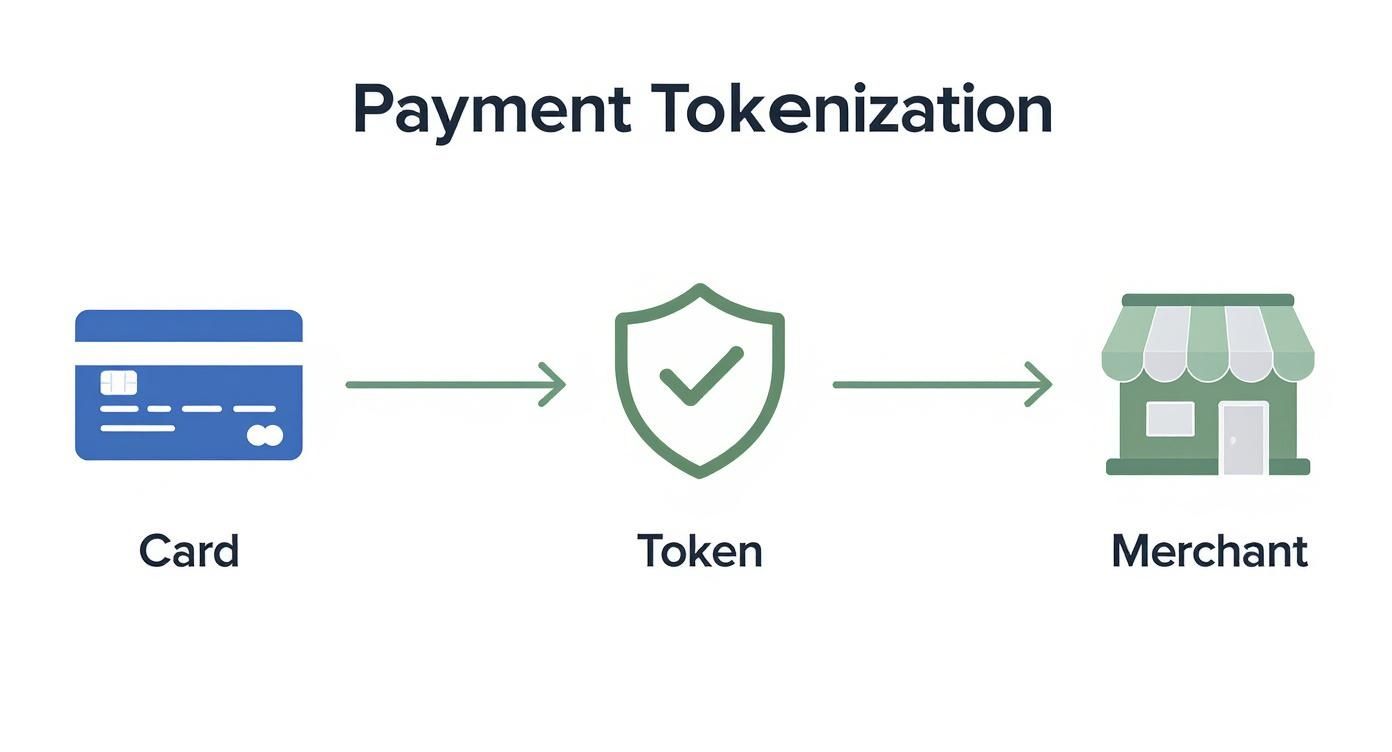
As you can see, the process is all about creating a secure barrier between your raw payment details and the business you're paying.
Step 2: The Token Request
Once the payment gateway gets the encrypted data, it shoots it over to a super-secure server called the token vault. This vault is the only place where sensitive payment info is briefly decrypted and handled, all within a protected, PCI-compliant environment.
The vault has two main jobs:
- It securely stores your real card number.
- It generates a completely new, random, and unique value—the token.
This token is then sent back to the payment gateway. It's crucial to understand that this token isn't mathematically linked to your card number in any way. It's just a placeholder with no real value on its own, making it impossible to reverse-engineer.
Step 3: Secure Storage and Token Usage
The payment gateway now passes this brand-new token to the merchant’s system. Finally, the merchant has something they can safely store in their customer records. Since the token is just a reference point and not sensitive data, it massively reduces the merchant’s security risk and makes their PCI compliance way simpler.
The biggest takeaway here is that the merchant’s systems never touch or store your actual card number. If the business ever had a data breach, hackers would only get their hands on a pile of useless tokens.
This is the secret sauce behind features like one-click checkouts and recurring subscriptions. When you come back to a store, the merchant just uses the stored token to start a new payment, so you don't have to re-enter all your details. For any online business, this is a must-have for building a smooth checkout experience that keeps customers coming back.
Step 4: Processing the Transaction
When it's time for the merchant to charge you—whether for that first purchase or a future one—they don't need your card number. Instead, they send the secure token back through the payment gateway.
The gateway forwards this token to the token vault, which securely looks up the actual card details associated with it. From there, it passes the real details to the card network (like Visa or Mastercard) to process the payment just like normal. This final step completes the secure loop.
The Core Benefits of Using Payment Tokenization
So, why has payment tokenization become such a big deal for businesses and shoppers alike? It’s not just tech for tech's sake. The answer is that it brings some serious advantages to the table, turning a complex security headache into a simple, elegant solution.
Ultimately, it all boils down to making payments safer, easier, and more convenient for everyone involved. When a business uses tokenization, it never actually stores your real credit card number. Instead, it holds onto a digital placeholder—a token.
If a data breach ever happens, what do the hackers get? Just a list of useless tokens. These tokens are completely worthless outside of that specific merchant’s payment system, making sensitive financial data a much less juicy target for cybercriminals.
Stronger Security and Fraud Prevention
By stripping sensitive card data from a merchant’s servers, tokenization directly slashes the risk of payment fraud. The numbers don't lie. Major card networks have seen a 30% reduction in online fraud on transactions that use tokens. You can learn about other powerful strategies in our guide to eCommerce fraud prevention.
This level of security is why the technology's adoption has absolutely exploded. By early 2025, Visa had already issued over 12.6 billion tokens, and Mastercard reported that about a third of all its global transactions were tokenized.
A huge side benefit is that tokenization also leads to higher approval rates. Visa actually saw a 4.6% lift in authorization rates for tokenized online transactions, which means fewer legitimate payments get declined by mistake.
A Smoother Customer Experience
But security is only half the story. Tokenization is a critical piece of any comprehensive fraud prevention strategy. For a wider view on how businesses tackle online financial crime, it's worth exploring other effective e-commerce fraud prevention tools.
Beyond the back-end security, tokenization dramatically improves the front-end shopping experience. It’s the magic behind the convenient features customers have come to expect:
- One-Click Checkouts: Securely stored tokens are what allow customers to buy something with a single click, without having to dig out their wallet and re-enter card details every single time.
- Recurring Payments: Think subscription boxes or streaming services. They use tokens to seamlessly and securely charge a customer’s saved card, ensuring there are no interruptions.
- Digital Wallets: Services like Apple Pay and Google Pay lean heavily on tokenization to keep your card information safe during contactless payments.
These features build trust and remove friction from the buying process, making it far easier for customers to complete a purchase and stay loyal to your brand.
Simplified PCI DSS Compliance
For any business that handles card payments, meeting the Payment Card Industry Data Security Standard (PCI DSS) is non-negotiable. But let's be honest—it’s a complex, costly, and time-consuming set of rules to follow.
This is where tokenization is a lifesaver. By making sure raw cardholder data never even touches a merchant's system, it drastically shrinks the scope of their PCI DSS assessment.
This saves businesses a ton of time, money, and headaches. It allows them to focus on what they do best—building great products and serving their customers—instead of getting bogged down in complicated compliance paperwork.
Tokenization vs. Encryption: What's the Difference?

People often throw the terms "tokenization" and "encryption" around as if they're the same thing, but they're fundamentally different ways of protecting data. Getting the distinction is key to seeing why tokenization is such a game-changer for securing payments.
Let's make it simple. Think of a sensitive credit card number as a secret document you need to protect.
Encryption is like locking that document inside an indestructible safe. You use a special key to lock it, and anyone who gets a copy of that key can unlock the safe and read the original document. The secret is still there, just scrambled up and locked away.
Tokenization, on the other hand, is like putting that same document through a shredder. Once it's destroyed, you get a unique claim ticket. This ticket has zero value on its own, but you can use it to reference the fact that you once had the document. The original, sensitive data is gone forever from your systems.
The Core Security Difference
The biggest difference boils down to one word: reversibility. Encrypted data can always be reversed back to its original form as long as you have the right key. This is great for data that's on the move, but it also creates a risk. If a hacker steals both the encrypted data and the key, they have everything they need.
Tokens, however, are a one-way street. They can't be mathematically reversed because a token is just a random placeholder, not a scrambled version of the original number. The only way to link a token back to the actual card data is through a highly secure, centralized token vault—which is kept far away from your business systems.
This is a massive deal when it comes to securing stored payment information. To see where this fits into the bigger picture, check out our detailed guide on how credit card transactions work.
For businesses, this means that even if their systems are breached, the stolen data is just a collection of useless tokens. Cybercriminals can't do anything with them because there's no "key" to unlock them and turn them back into usable card numbers.
Tokenization vs. Encryption: A Head-to-Head Comparison
To make it even clearer, let’s put the two methods side-by-side. Seeing how they stack up helps highlight why they are used for different jobs within a secure payment process.
Ultimately, both are crucial security tools, but they solve different problems. Encryption protects data as it travels, while tokenization removes the data from your environment entirely, drastically reducing your risk and PCI compliance burden.
The Future of Payment Security with Tokenization

Tokenization isn’t some static, set-it-and-forget-it technology. It’s constantly moving, shaping the very future of how we handle payments. As digital commerce keeps expanding, tokenization is evolving right there with it, pushed forward by new consumer habits and the relentless need for smarter, stronger security.
The growth we're seeing is staggering. The global tokenization market, valued at around USD 3.51 billion in 2024, is projected to rocket to USD 25.2 billion by 2035. This incredible surge is being fed by the boom in digital wallets, the ease of contactless payments, and the ever-growing network of connected devices (the Internet of Things).
The Rise of Network Tokenization
One of the biggest shifts pushing this evolution is network tokenization. Unlike the older method where a payment gateway created the token, these new tokens come straight from the big players: Visa, Mastercard, and American Express.
This is a game-changer for a few critical reasons:
- Tighter Security: Network tokens are locked to a specific device and can be managed on the fly, adding a powerful new shield against fraud.
- Better Approval Rates: With the card issuer directly involved in the token's creation, transactions are seen as more trustworthy. This leads to higher authorization rates and less money lost to frustrating false declines.
- Automatic Card Updates: This one is huge for subscription businesses. When a customer’s physical card expires or gets replaced, the network token updates automatically. No more awkward conversations or canceled services.
Network tokenization is rapidly becoming the new gold standard. It makes sure that saved card details stay current and secure, which is a lifeline for businesses relying on recurring revenue and a frictionless customer experience.
Beyond Just Payments
The core idea of tokenization—swapping sensitive data for a useless placeholder—has legs that reach far beyond credit card numbers. As our lives become more digital, this technology is being used to protect all kinds of confidential information.
Think about securing personally identifiable information (PII) like social security numbers, private health records, or even driver's license details. This is absolutely critical for any organization handling sensitive personal data. By tokenizing this info, companies can dramatically cut down their risk profile and make it much easier to comply with data privacy laws.
This forward-thinking approach is a cornerstone of modern security and works hand-in-hand with robust transaction monitoring solutions.
For a wider view, it's worth exploring broader strategies to enhance fintech app security to see how these pieces fit together. The simple principle of swapping out valuable data for a secure stand-in is becoming a fundamental building block of our entire digital world, promising a safer future for every kind of data.
Common Questions About Payment Tokenization
Even after breaking down the process, it's natural to have a few more questions about what payment tokenization really means for your business. Let's tackle some of the most common ones to clear up any lingering confusion.
Think of this as the practical, real-world guide to using tokens for everything from monthly subscriptions to one-off purchases.
Is Tokenization Completely Foolproof?
It's tempting to think of tokenization as a magic bullet for security, but the truth is, no single technology is completely foolproof. While it's an incredibly powerful tool for protecting data, it works best when it's part of a bigger security plan.
Think of it like the deadbolt on your front door—it's your strongest lock, but you still need to lock your windows and set the alarm.
Tokenization brilliantly protects stored payment data by making it useless to thieves. If a company's database gets breached, hackers walk away with a pile of worthless tokens instead of valuable card numbers.
However, a complete security strategy also includes:
- Encryption to protect data while it's traveling from a customer's browser to the payment gateway.
- Fraud detection systems that actively monitor for unusual transaction patterns.
- Strong internal controls to ensure only authorized personnel can access sensitive systems.
When you layer these defenses together, you create a formidable barrier that makes it extremely difficult for criminals to succeed.
How Does Tokenization Work with Subscriptions?
Tokenization is the secret sauce that makes recurring payments, like subscriptions, both seamless and secure. When you sign up for a service—say, a streaming platform or a monthly delivery box—the company doesn't actually store your credit card number. Instead, it tokenizes your card details during that very first payment.
From that moment on, the company holds onto the secure token, not your sensitive financial information.
Each month, when your subscription is due, the business simply sends that same token to its payment processor to kick off the charge. The system works just as we've described: the token is sent to the vault, the real card data is pulled up in that secure environment, and the payment is processed.
This means you never have to re-enter your details, and the business never has to risk storing your card number on its servers. It’s a win-win that delivers convenience for the customer and drastically cuts risk for the company.
For a deeper dive into common queries, you can explore our full ChargePay FAQs page.
Can the Same Token Be Used at Different Stores?
That's a great question, and the answer usually depends on the type of token being used. In most cases, the answer is no—and that’s actually a good thing for your security. The most common type of token is specific to a single merchant.
Here's how the different types break down:
- Merchant-Specific Tokens: When you save your card at an online store, that business typically gets a token that is locked to them. It absolutely cannot be used to make a purchase at any other store. If a hacker managed to steal that token, it would be completely useless anywhere else.
- Network Tokens: These are more flexible tokens issued directly by card networks like Visa and Mastercard, often used in digital wallets like Apple Pay and Google Pay. While more versatile, they have their own advanced security features that tie them to a specific device or customer, keeping them just as secure.
So, while you can't take a token from your favorite clothing store and use it to buy coffee, this limitation is a core part of what makes the whole system so secure. Each token is locked into its own little ecosystem, preventing it from ever being misused.
Ready to stop losing revenue to chargebacks? With ChargePay, you can automate your dispute process and recover up to 80% of lost funds. Our AI-powered solution generates winning responses in real time, so you can focus on growing your business. Protect your revenue with ChargePay today.






.svg)







.svg)
.svg)
.svg)